The eval() Function in Python
- What is eval() in Python?
- Using eval() with Variables
- Security Concerns with eval()
- Alternatives to eval()
- Conclusion
- FAQ
In the world of Python programming, the eval() function often sparks curiosity and debate among developers. It’s a powerful built-in function that evaluates a string expression and executes it as Python code. While this functionality can be incredibly useful, it also comes with its fair share of risks, especially when it comes to security.
In this tutorial, we will dive deep into what the eval() function does, how it works, and when it’s appropriate to use it. By the end of this article, you’ll have a solid understanding of eval() and be equipped to make informed decisions about its use in your Python projects.
What is eval() in Python?
The eval() function in Python takes a string expression and evaluates it as a Python expression. This means you can pass a string containing a Python expression, and eval() will return the result of that expression. The syntax for the function is straightforward:
result = eval(expression, globals=None, locals=None)
Here, expression is the string you want to evaluate, while globals and locals are optional parameters that allow you to specify the global and local namespace in which the expression is evaluated.
Example of eval() Usage
Let’s look at a simple example to illustrate how eval() works.
expression = "3 * 5 + 2"
result = eval(expression)
print(result)
Output:
17
In this example, the string “3 * 5 + 2” is evaluated, and the result is calculated as 17. This shows how eval() can dynamically execute code contained in a string.
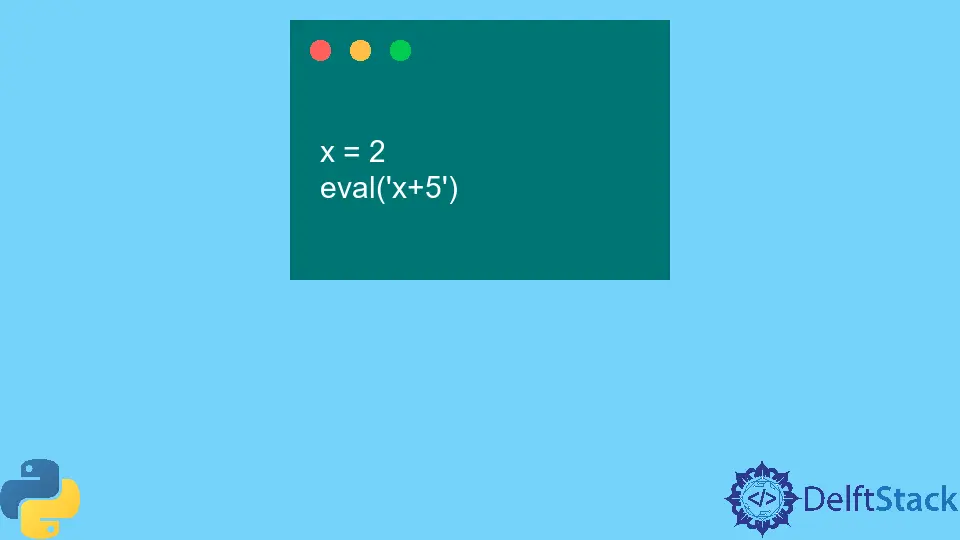
Using eval() with Variables
One of the most interesting aspects of eval() is its ability to interact with variables defined in your Python script. This means you can evaluate expressions that use variables, making it a flexible tool for dynamic calculations.
Example of eval() with Variables
Consider the following code where we use variables in an expression.
a = 10
b = 20
expression = "a + b * 2"
result = eval(expression)
print(result)
Output:
50
In this case, eval() evaluates the expression “a + b * 2”, using the current values of a and b. The result is calculated as 50, demonstrating how eval() can incorporate variable values into its evaluations.
Security Concerns with eval()
While eval() is a powerful tool, it’s crucial to be aware of the security implications associated with its use. Since eval() will execute any code passed to it, there is a risk of executing malicious code if the input is not properly sanitized. This makes eval() a potential target for code injection attacks.
Mitigating Security Risks
To mitigate these risks, it’s essential to avoid using eval() with untrusted input. If you must use it, consider implementing strict validation checks or using safer alternatives like ast.literal_eval() for evaluating simple data structures.
Example of Unsafe eval() Usage
user_input = "__import__('os').system('ls')"
result = eval(user_input)
print(result)
Output:
# This could execute a command in the OS, which is dangerous.
In this example, if user_input comes from an untrusted source, it could potentially execute harmful commands. Always be cautious and validate inputs when using eval().
Alternatives to eval()
If you find yourself needing to evaluate expressions but are concerned about the risks associated with eval(), there are safer alternatives. One such alternative is the ast.literal_eval() function, which safely evaluates strings containing Python literals.
Example of ast.literal_eval()
Here’s how you can use ast.literal_eval() to safely evaluate expressions:
import ast
expression = "[1, 2, 3, 4, 5]"
result = ast.literal_eval(expression)
print(result)
Output:
[1, 2, 3, 4, 5]
In this example, ast.literal_eval() safely evaluates the string as a list of integers. This method is much safer than eval() because it only allows certain Python literals and raises an exception for anything else, making it a more secure choice for evaluating user input.
Conclusion
The eval() function in Python offers powerful capabilities for evaluating string expressions, but it comes with significant security risks. Understanding how to use eval() effectively, along with its alternatives, is crucial for writing safe and secure Python code. By being cautious and validating inputs, you can harness the power of eval() while minimizing potential vulnerabilities. Always consider whether you truly need to use eval() or if a safer alternative might be more appropriate for your needs.
FAQ
-
What is the purpose of the eval() function in Python?
The eval() function evaluates a string expression and executes it as Python code. -
Is eval() safe to use?
eval() can be unsafe if used with untrusted input, as it may execute malicious code. -
What are some alternatives to eval()?
Safer alternatives include ast.literal_eval() for evaluating simple data structures. -
How does eval() handle variables?
eval() can evaluate expressions that include variables defined in the current scope. -
Can eval() execute any Python code?
Yes, eval() can execute any valid Python expression, which is why it poses security risks.