How to Secure Sensitive Information in Django on GitHub
Building projects and software and sharing them with the world on GitHub is a fun and exciting process. We relish to add exciting and compelling features to our applications and push the code to GitHub using git. Still, sometimes we tend to forget about one of the most critical aspects of software development: security.
When building software, we have to ensure that the software is safe and doesn’t have potential loopholes for a data breach.
Django, the web framework, comes with robust security. The authentication system of Django is mighty. Django has a settings.py where most of the sensitive data is present. Hence, storing such a file on GitHub could be a dangerous decision.
But don’t worry. There are a few ways to push the code on GitHub and ensure safety at the same time.
Secure Sensitive Information in Django using Environment Variables
Environment variables are some variables whose values are stored outside the program, and they are read from the program to access the information. These variables are stored in a .env file.
First, create a file .env. Then, inside the .gitignore file, add .env. This addition will make sure that the .env file is not uploaded to GitHub.
Now you will need a Python Package to deal with these files. The package name is Decouple. Use the following pip command to install the package.
pip install python-decouple
Or,
pip3 install python-decouple
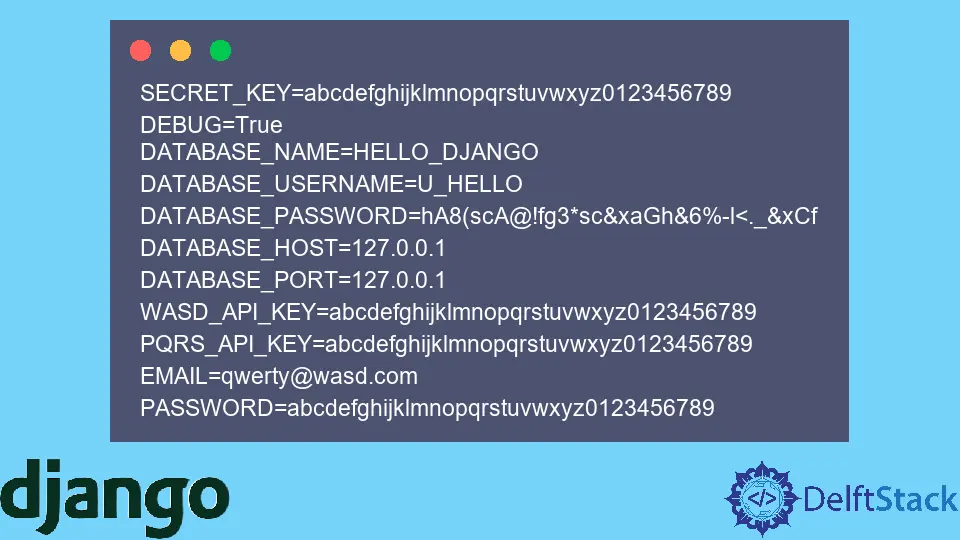
Inside the .env file, add the sensitive information. This information could be your Django project secret key, your database credentials, your email id and password, your API keys, etc. The Decouple Python Package will automatically look for this file inside the Django project.
Store the information in the following manner. Make sure that you follow the same syntax: no spaces included before and after the = sign and no quotation marks added to represent the strings.
SECRET_KEY=abcdefghijklmnopqrstuvwxyz0123456789
DEBUG=True
DATABASE_NAME=HELLO_DJANGO
DATABASE_USERNAME=U_HELLO
DATABASE_PASSWORD=hA8(scA@!fg3*sc&xaGh&6%-l<._&xCf
DATABASE_HOST=127.0.0.1
DATABASE_PORT=127.0.0.1
WASD_API_KEY=abcdefghijklmnopqrstuvwxyz0123456789
PQRS_API_KEY=abcdefghijklmnopqrstuvwxyz0123456789
EMAIL=qwerty@wasd.com
PASSWORD=abcdefghijklmnopqrstuvwxyz0123456789
As mentioned above, we generally and should keep all the sensitive data in the settings.py file. We’ll do the same here as well, but we will not directly add the values. We will read them from this .env we just created.
Inside the settings.py, we can retrieve the above values as follows.
import os
from decouple import config
BASE_DIR = os.path.dirname(os.path.dirname(os.path.abspath(__file__)))
SECRET_KEY = config("SECRET_KEY") # Here
DEBUG = config("DEBUG", cast=bool) # Here
DATABASES = {
"default": {
"ENGINE": "django.db.backends.postgresql_psycopg2",
"NAME": config("DATABASE_NAME"), # Here
"USER": config("DATABASE_USERNAME"), # Here
"PASSWORD": config("DATABASE_PASSWORD"), # Here
"HOST": config("DATABASE_HOST"), # Here
"PORT": config("DATABASE_PORT", cast=int), # Here
}
}
WASD_API_KEY = config("WASD_API_KEY")
PQRS_API_KEY = config("PQRS_API_KEY")
EMAIL = config("EMAIL")
PASSWORD = config("PASSWORD")
config has a cast parameter that defines to which data type the value should be cast to. By default, Decouple reads all the values as strings. Hence, this cast parameter can be used to cast the values to the desired data type.
That’s it. Now, all the sensitive data is safe in a .env file, and as long as you don’t upload this file to GitHub, the information is secure. Moreover, the project will not break either because the variables are intact where they were present previously. The only thing that has changed is the way we assign them values.
